They say that a chain is only as effective as its weakest link. Information Security (IS) professionals describe that as the single point of failure. When cybercriminals probe your company’s IT systems, they’ll typically search for that weakest point. The best way to preempt becoming a victim of cybercrime, therefore, is to create robust threat management capabilities. And the threat intelligence tools you choose to acquire that capability may be your organization’s weakest link!
Inside the Minds of Cybercriminals
According to global research company Gartner, the information security market will have grown to a $170.4 billion marketplace shortly, growing at a 5-year compound annual growth rate (CAGR) of 8.5%. For cybercriminals, that prospect should be a deterring factor but, unfortunately, it isn’t! That’s because the bad actors of cyberspace know that cyber–Incident Response (IR) teams lack the necessary tools and capabilities to forewarn them of impending threats.
Cybercriminals also know that, while third party threat intelligence services and tools are available to aid and assist them, many organizations don’t take the threats seriously enough to engage those services. As a result, the bad guys follow a well-orchestrated playbook:
- They’ll test for vulnerabilities: They often check for weak areas in a company’s IT infrastructure. These may be known software bugs, erroneous configuration items, weak passwords, outdated patches…and complacent, uninformed users!
- They’ll exploit the vulnerabilities: They exploit those weakest links using an array of tactics and strategies. They’ll use psychological manipulation through social engineering or phishing scams, or malware, deceptive links, “loaded” scripts, scanners or infected code to launch their attacks.
In the absence of up-to-date threat intelligence to warn them, or the appropriate threat intelligence tools to protect them, most security operations centers (SOC) are no match for cybercriminals. In some instances, the attackers are in business within minutes of detecting a vulnerability.
Boost Your Threat Management Capabilities
The only way for organizations to fight back, is to boost their own threat management capacities. And to do that, IS teams must build those capabilities by streamlining their threat analysis and response abilities. However, not every organization can build their own tools, or engage an army of threat analysts and data accumulators and compilers, or maintain hundreds of gigabytes of TI data. That’s why it’s important work with external tools and service providers that specialize in those capabilities.
Quolab’s threat intelligence services helps IR teams leverage the best cyber tools and capabilities available today. By automating threat intelligence, IS professionals can empower their in-house Security Operations Platform (SOP) to proactively mitigate any vulnerability, or attempts to exploit them.
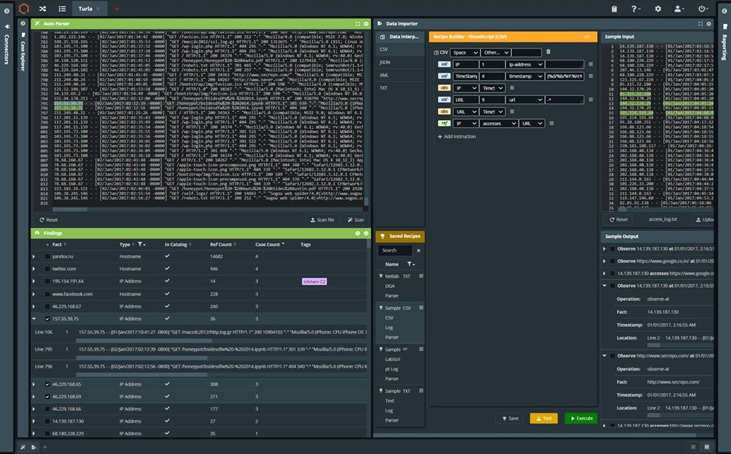
The platform is optimized to flatten the threat response org structure so that there are fewer barriers to mounting an effective response. It’s also adept at breaking down traditional information silos that slow down threat responses. Native integration with a host of leading cyber threat data vendors, such as Mandiant, WhoIsXML, Domain Tools, VMRay, and Binary Ninja, and full support for MISP, STIX, OTX, YARA, HTML, and an array of other “open” threat feeds, gives an added layer of proactive protection to your information security (IS) platforms, and eliminates that weakest link that cybercriminals can exploit.
